Find Which Hash Type of Use and Password Linux
Passwords should never be stored as plain text. Passwords should be hashed with either PBKDF2 bcrypt or scrypt MD-5 and SHA-3 should never be used for password hashing and SHA-12 passwordsalt are a big no-no as well.
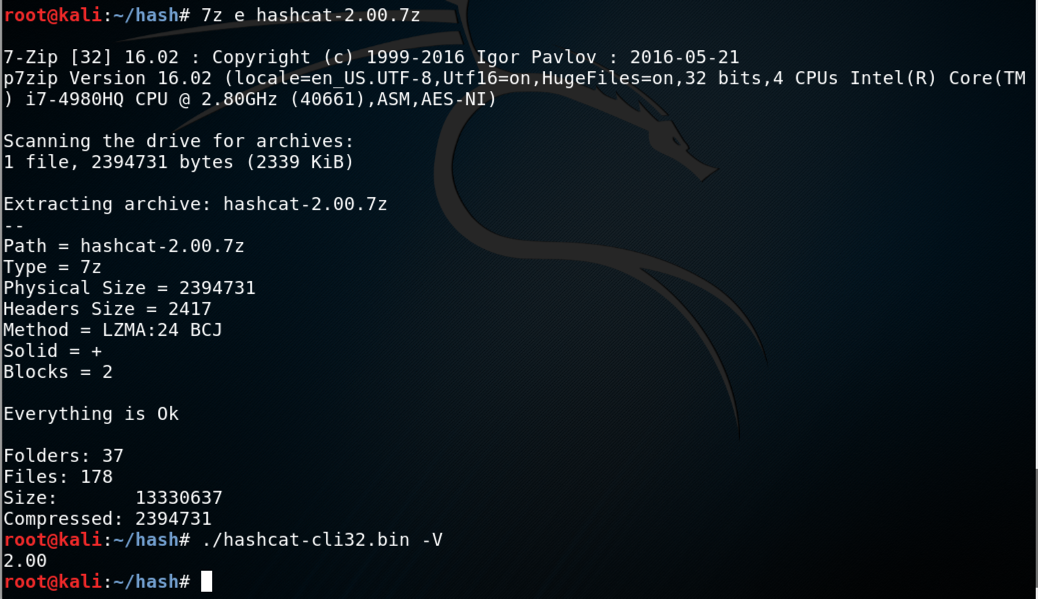
Project 12 Cracking Linux Password Hashes With Hashcat 15 Pts
I know that the etcshadow file hash follows this syntax.
. Otherwise its crypts default DES algorithm with a 13-character hash or big crypts DES extended to support 128-character passwords with hashes up to 178 characters in length or BSDI extended DES with a _ prefix followed by a 19-character hash. Linux uses etcshadow. This page will tell you what type of hash a given string is.
Only root user can write inside this file. Right-click on a file or a set of files and click Hash with HashTools in the context menu. After implementing shadow-utils passwords are now saved in etcshadow file in Linux.
The password should be minimum 8-12 characters long including special characters digits lower case alphabetic and more. Use the below commands from the Linux shell to generate hashed password for etcshadow with the random salt. How do I find the hash value of a file.
Along with hashed password this file also stores content like username password change date expiry date etc. Note that a password hash function is a particular type of cryptographic hash function which is not used for other uses of cryptographic hash functions. Dont worry here i listed different types of Hash codes.
The id identifies the algorithm being used eg. PBKDF2 isnt bad either but if you can use bcrypt you should. Here is an entry of my shadow file.
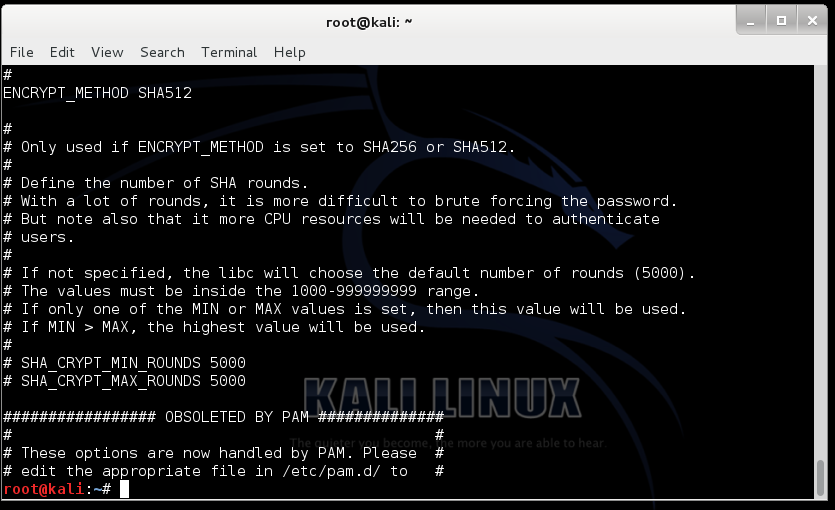
1 is MD5 2a is Blowfish 2y is Blowfish 5 is SHA-256 6 is SHA-512. 1 2 Domain Cached Credentials. Ubuntu stores password content in file etcshadow.
A tool for identifying cipher hash type is available upon typing hash values. As a general suggestion posting your password hash on public forums is not necessarily a good idea. Debian sudo apt-get install p7zip p7zip -d hashcat-2007z cd hashcat-200 Red Hat sudo yum install p7zip 7za x hashcat-2007z cd hashcat-200 Next the commands will be the same for Debian and Red Hat systems.
By looking at the etcshadow file as root you will be able to see which hash is used on your linux. To use the sha512 algorithm instead we have to use the -6 option. Include all possibilities expert mode Submit Identify.
If you want to attempt to Decrypt them click this link instead. So if a hashed password is stored in the above format you can find the algorithm used by looking at the id. In our example the salt is the string Iv then there follows the actual hash.
You can put passwords in etcpasswd its still supported for backward compatibility but you have to reconfigure the system to do that. Openssl passwd -6 Password. How to Hash Passwords in Linux.
This launches the HashTools program and adds the selected files to the list. The MD5 algorithm is often used to find etcshadow files for username and password management in Linux. Lets see the contents of the etcshadow file and also its permission.
There are a handful of different password hashes usually used for Linux system users passwords theyre listed in the man page for crypt 3 The first is the original crypt algorithm that only supported 8 character passwords among other flaws and which youll hopefully never see again. The first two characters of the field indicate the hash type being used. Usually password format is set to idsalthashed The id is the algorithm used On GNULinux as follows.
By default the command uses the crypt algorithm to generate an hashed password. How to manually generate checksums Using the hash utilities is very simple. I will do so.
Identifying the types of hashing used in data encryption as well as particular passwords is possible with this tool. Before making use of the Linux command to generate a SHA-256 hash we must know what SHA actually is and what it is good for. In this case 6 or SHA512.
Print cryptcrypt MySecretPassword 1s randomsalt --- 1YjOzcqrfZqx4sx5CQRuEIFCdOLAJV0. Whether we are talking about a web application or an operating system they should always be in the hash form on Linux for example hashed passwords are stored in the etcshadow file. 1 members found this post helpful.
Of course you were probably using a test password but its still worth saying. Perform the following for your Linux type. The password hash is in the second field of the etcshadow file.
This etcshadow file is only accessible by root. Password hashes were traditionally stored in etcpasswd but modern systems keep the passwords in a separate file from the public user database. Currently the most vetted hashing algorithm providing most security is bcrypt.
Randomsalt join randomsample stringascii_letters8. The user name and 5 Characters at the beginning of the password hash are missing. It is an algorithm on its own that is able to generate an almostunique and fixed size 256-bit32-byte hash.
What Hash Type Is Used By Linux. - I wish to know what problems it might cause because I had issues in the past that I could not find a root for. 1 MD5.
If you want to sign something with a hash most Unices will integrate the binary. If this hash represents an actual password you use you should consider this password compromised and change it everywhere. Generate MD5 password hash.
Here is what we would write. Does anybody know if this might cause problems. Python -c import randomstringcrypt.
Please dont tell me to remove the line. IvS7aeT4NzQPM Used in Linux and other similar OS. Hashing is the process through which by the use of complex algorithms a.
As a result of these vulnerabilities MD5 hash function vulnerability has been severely compromised. Identify and detect unknown hashes using this tool. There are two files you need to be aware of in this folder.
Password File Location and Content. We will focus on the second field ie salt with hashed password. In colon separated format.
How Do I Know If My Hash Is Md5 Or Sha256. 2a Blowfish not in mainline glibc. Shadow utils is a package in Linux thats installed by default in most of the distributions used for separating passwords from etcpasswd.
The first two characters are the salt random characters. For this tool select hash-identifier from the command line. Added in some Linux distributions 5 SHA-256 since glibc 27 6 SHA-512 since glibc 27 If you see 6 then SHA-512 is used.
Next click on a hashing algorithm eg CRC MD5 SHA1 SHA256 etc to generate the hash checksum for the files. In other words. SHA-256 in very simple terms is a cryptographic hash function that has a digest length of 256 bits.
The second is the MD5-based md5crypt a b marked with 1.
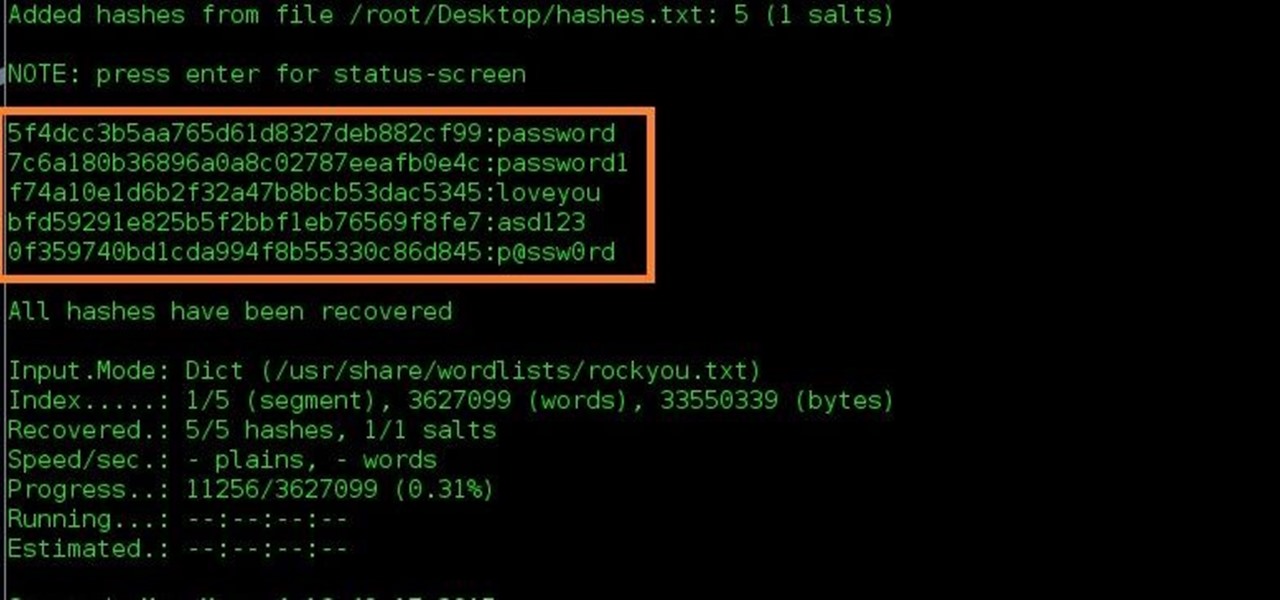
How To Identify And Crack Hashes Null Byte Wonderhowto

Project 12 Cracking Linux Password Hashes With Hashcat 15 Pts

No comments for "Find Which Hash Type of Use and Password Linux"
Post a Comment